Background
As of now, we are using default directory for authorizing
users for Hyperion EPM System in Vodafone.
Default directory is native directory - refers to the
Lightweight Directory Access Protocol (LDAP)-enabled user directory that Shared
Services uses to support provisioning.
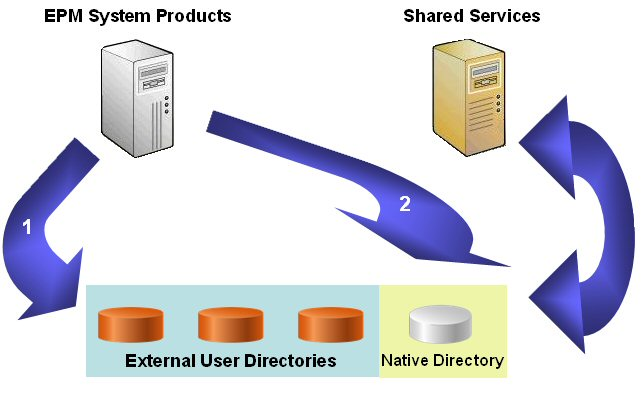
What is User Directory
User directories refer to any corporate user and identity
management system compatible with Shared Services.
Supported User
directories
·
OID
·
Sun Java System Directory Server (formerly
SunONE Directory Server)
·
Microsoft Active Directory
·
custom-built user directories that implement
LDAP version 3
·
Windows NT LAN Manager (NTLM)
·
SAP native repository
We can configure one or more user directories along with
native directory in shared services for EPM System.
User Directory functions:
·
Used to
maintain and manage the default Shared Services user accounts required by EPM
System products
·
Central
storage for all EPM System provisioning information because it stores the
relationships among users, groups, and roles
Single Sign On
(SSO) for EPM system using User Directory
·
Through a browser, users access the EPM System product
login screen and enter user names and passwords.
·
The Security API implemented on the EPM System
product queries the configured user directories (including Native Directory) to
verify user credentials. A search order establishes the search sequence. Upon
finding a matching user account in a user directory, the search is terminated,
and the user's information is returned to the EPM System product.
·
Access is denied if a user account is not found
in any user directory.
Configuring MSAD
Open shared services console
Administration à
Configure User directory
1. MSAD Connection information
·
Directory
server – populated automatically depending upon the user directory selected
for configuration. As we selected, MSAD, Microsoft is populated here.
·
Name
– It is for our reference. We can give any name here.
·
DNS
Lookup and Host Name –
o DNS Lookup – When HA is implemented, we can use this
option. IF the main MSAD server fails,
we can switch to the backup server which is registered to the same DNS name.
o Host
Name – This option is used when HA is not implemented. When user enters
credentials in EPM system, the user is searched in MSAD server which is located
with the host name given.
As HA is not implemented in our
case, we should be using Host Name.
·
Port –
User Directory port (389 is for MSAD)
·
Base DN
– The distinguished name (DN) of the node where the search for users and groups
should begin. Without filling anything, click “Fetch DNs” button and then
select one of the listed DNs
·
ID
Attribute – This attribute must be a common attribute that exists in user
and group objects on the directory server.
The recommended value of this attribute is automatically set for OID orclguid, SunONE (nsuniqueid), IBM Directory Server (Ibm-entryUuid), Novell eDirectory (GUID), and Active Directory (ObjectGUID).
The recommended value of this attribute is automatically set for OID orclguid, SunONE (nsuniqueid), IBM Directory Server (Ibm-entryUuid), Novell eDirectory (GUID), and Active Directory (ObjectGUID).
·
Maximum
size – it sets the limit on number of maximum users retrieved during
search. We have set this limit as 500 as
retrieving all users from domain takes huge time.
·
Trusted –
if it is trusted SSO source.
·
Anonymous bind – ignore this
right now. (To give search permission to particular users
·
User DN – This is the distinguished name of user
that will be used by Shared Services to configure.
To get DN, we can search it in
registry after logging into domain with same user credential.
We did not go for advanced options this time and can be
covered later.
2.
MSAD User
Configuration
Data entry in this user configuration screen is optional.
If we do not enter any user information here, Shared Services searches for all
users present in Base DN.
As we think, this will definitely affect the performance.
But we are going to manage performance by restricting user search to 500 in
first step and then configuring with a particular group instead of the whole
base DN.
So, we just kept the user configuration screen blank and
moved ahead.
3.
MSAD Group
Configuration
The final step is MSAD group configuration.
Here, in the unique identifier box, enter correct name of
group in domain and press auto configure. This will populate your group RDN.
In the second box,
Name Attribute – we have filtered user Admin from MSAD
directory. Admin user will be used only
from native directory. We were getting following error before trying this
option.
2014-01-14 10:50:59,295 ERROR [[ACTIVE] ExecuteThread:
'1' for queue: 'weblogic.kernel.Default (self-tuning)']
com.hyperion.css.spi.impl.msad.MSADProvider.authenticate(Unknown Source) --
60:1005:Authentication failed for user admin. Enter valid credentials.
In the last box, we have limited domain users only to
specific group. You can create a particular group for Hyperion users in domain
and provide the group name here so that the performance will be good.
Once we finish this step, we need to logoff from Shared
Services console.
Then we can see MSAD directory in the directory list in
Shared Services Console.
When logged off after MSAD configuration from shared services, I was not able to see the new directory under User directories.
*****************************************************************************
We need to restart foundation services service i.e. HyS9FoundationServices - Hyperion Foundation Services - Managed Server from services.
This showed the new added directory under user directories
******************************************************************************








FreedomPop is Britian's #1 ABSOLUTELY FREE mobile phone provider.
ReplyDeleteVoice, text & data plans starting at £0.00/month.
How to deactivate directory?
ReplyDelete